Understand How Hash Functions Keep Bitcoin Transactions Safe
When people talk about Bitcoin’s security, the term “hash function” often comes up. It might sound technical, but it plays a vital role in how transactions stay trustworthy. Every time someone sends or receives Bitcoin, a hash function helps verify the action behind the scenes.
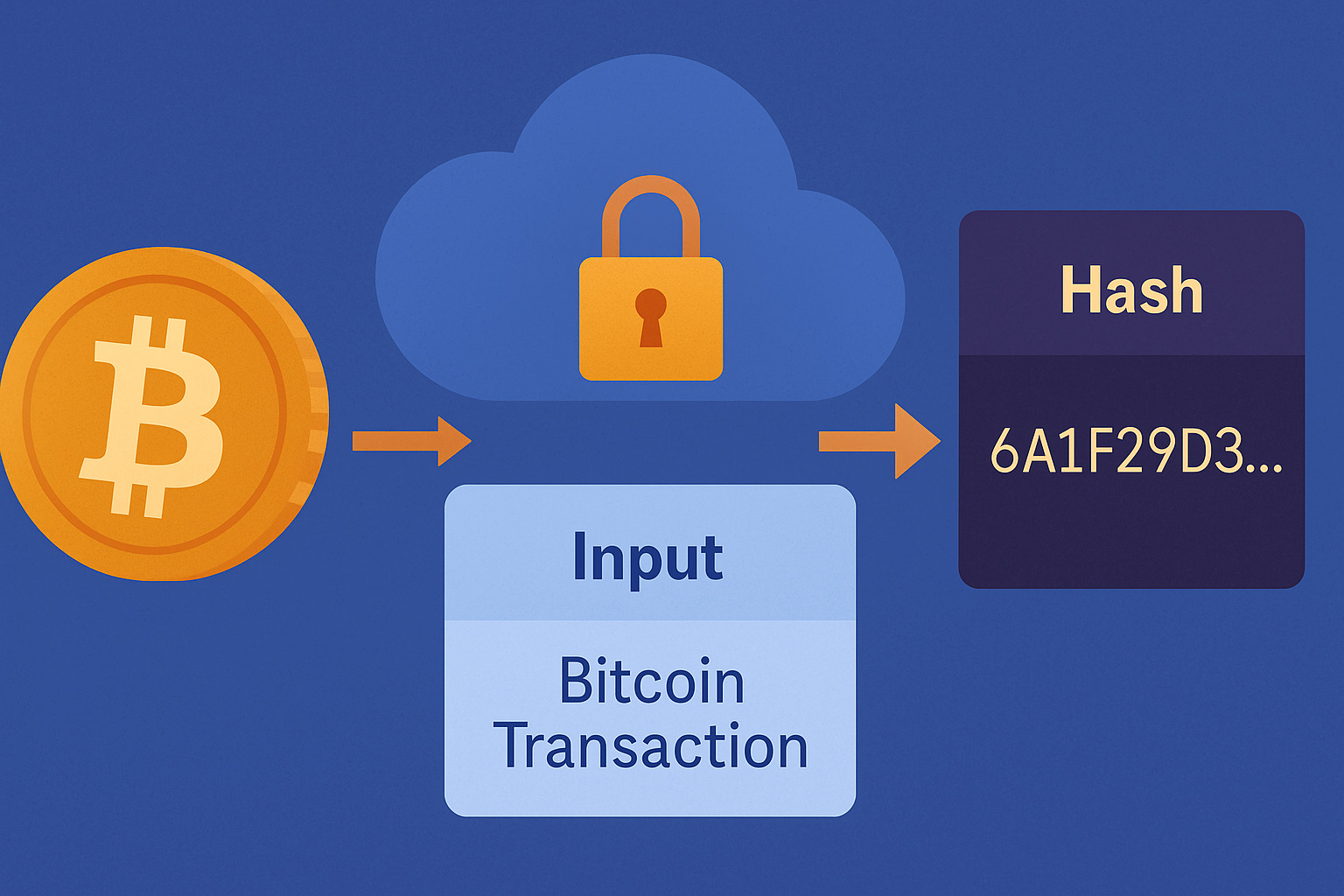
A hash function is like a fingerprint generator for data. It takes information—like a Bitcoin transaction—and creates a unique string of characters. Even the smallest change in the input changes the output completely. This makes tampering nearly impossible to hide.
What makes this system powerful is that these hashes are used throughout the Bitcoin network. They confirm transactions, link blocks together, and make sure nobody can fake or duplicate a transfer. Without hash functions, the entire idea of Bitcoin would fall apart.
How SHA-256 Hashing Works in the Bitcoin Network
Bitcoin uses a specific type of hash function called SHA-256. This stands for Secure Hash Algorithm 256-bit. It takes any kind of input and produces a fixed-length result of 64 characters. The output doesn’t show any direct clues about the input.
When a transaction is created, Bitcoin software runs it through SHA-256. The result is a hash that represents the transaction. This hash becomes part of the record that gets sent to the blockchain for verification and storage.
SHA-256 is designed to be one-way. You can go from input to output, but not the other way around. That makes it secure. Even if someone sees the hash, they can’t reverse it to get the original data. This one-way street adds a strong layer of protection.
Linking Transactions Together With Hashes
In Bitcoin, every block contains a set of transactions. These transactions are grouped and linked together using hashes. Instead of just being a list, the transactions are combined into a data structure called a Merkle tree.
A Merkle tree takes pairs of transaction hashes and combines them, then hashes the result again. This process repeats until one single hash—called the Merkle root—is produced. That root summarizes all the transactions in a block.
If someone tries to change even a small detail in one transaction, the Merkle root changes too. This makes it easy to detect tampering. Miners and nodes in the network use the Merkle root to quickly verify that every transaction in a block is valid and untouched.
Protecting Blocks With Hash Pointers
Not only are transactions protected by hashes, but blocks themselves are linked together through something called hash pointers. Each block contains the hash of the previous block. This forms a long, secure chain—hence the name “blockchain.”
Because the hash depends on the data inside the previous block, any change to an earlier block will completely alter its hash. That means all following blocks would no longer match their pointers. The chain would break, and the network would reject it.
This setup makes Bitcoin tamper-resistant. Trying to rewrite the blockchain would require changing not just one block, but all blocks that come after it. And since the network compares all new entries to the shared chain, it won’t accept altered versions.
How Miners Use Hashes to Find New Blocks
Miners do more than confirm transactions—they compete to find new blocks. They do this by solving a special kind of math puzzle that involves hashes. This process is known as Proof of Work.
To mine a block, a miner has to find a special number called a nonce. When combined with the block’s data and passed through SHA-256, this nonce must produce a hash that starts with a certain number of zeroes. It’s like a lottery where millions of tries are needed to win.
This puzzle doesn’t serve a mathematical purpose on its own, but it adds security. Because finding the right hash takes time and effort, it prevents people from spamming or flooding the network with fake data. The first miner to find the right answer adds the new block and earns a reward.
Confirming Valid Transactions Through Hash Verification
Once a miner includes a transaction in a block, other computers in the Bitcoin network double-check it. They do this by recalculating the hash. If the result matches what the block shows, the transaction is considered valid.
This step happens automatically. Every full node in the network runs this verification process. It’s how Bitcoin stays decentralized—there’s no one authority deciding what’s real. The code and the hash checks keep everyone honest.
If any part of the transaction is off, the hash won’t match. That transaction gets rejected. Hashes act like digital signatures, allowing users and machines to know exactly what data they’re dealing with, without needing to see all the internal details.
Preventing Duplicate Transactions With Unique Hashes
Each transaction in Bitcoin gets a unique hash. This hash serves as an ID and ensures that no transaction is counted more than once. If someone tries to submit the same transaction again, the network spots the duplicate hash and blocks it.
This process protects against double spending. That’s when someone tries to send the same bitcoin to two different places. The network only accepts the first valid transaction hash and ignores any later copies.
Because hashes are so sensitive to change, even a slight modification creates a totally different hash. That’s why attackers can’t trick the system by submitting slightly altered versions of old transactions. Bitcoin’s rules make sure each hash can only represent one action.
Handling Privacy and Transparency in Public Ledgers
Bitcoin’s blockchain is public, meaning anyone can see transaction data. But thanks to hashes, the details are hidden from casual view. The hash function doesn’t expose private information like names or passwords—it only displays coded outputs.
This setup lets Bitcoin maintain transparency without revealing identities. Every transaction is traceable through hashes and addresses, but users stay anonymous unless they choose to link themselves publicly to an address.
While hash functions don’t provide full privacy, they play a major role in making the network open and verifiable. The public can audit the blockchain, but personal details remain out of reach, keeping user data protected by design.
Why Hash Security Helps Bitcoin Stay Decentralized
Bitcoin’s structure depends on wide participation. Users, miners, and developers all contribute to keeping the system running. Hash functions make this possible by allowing machines across the world to agree on what’s valid and what’s not.
By relying on a set of cryptographic rules, Bitcoin avoids the need for a central decision-maker. Instead, every participant checks hashes independently. This shared agreement forms the basis of trust within the network.
Without hash functions, decentralization would be much harder to manage. The math behind the hashes lets people work together, even if they don’t know or trust each other. It’s a key piece of what makes Bitcoin function the way it does.
Bitcoin Security Relies on Strong Hash Integrity
Every part of Bitcoin—transactions, blocks, mining, verification—depends on hash functions. These tiny lines of code carry enormous responsibility. They keep the system honest, prevent fraud, and ensure the blockchain reflects only what’s real.
The strength of SHA-256 lies in its simplicity and reliability. It doesn’t need constant updates or complex rules. It quietly powers a global network of value, proving every day that strong security doesn’t need to be flashy—it just needs to work.
For anyone using Bitcoin, understanding hash functions offers peace of mind. These invisible tools work in the background, making sure your transactions reach the right place, stay safe from tampering, and remain part of a secure, growing chain.














No Responses